| Drawbacks of DHCP |
|---|
| Network Security Vulnerability |
| Availability Dependency |
| IP Address Exhaustion |
| Management Overhead |
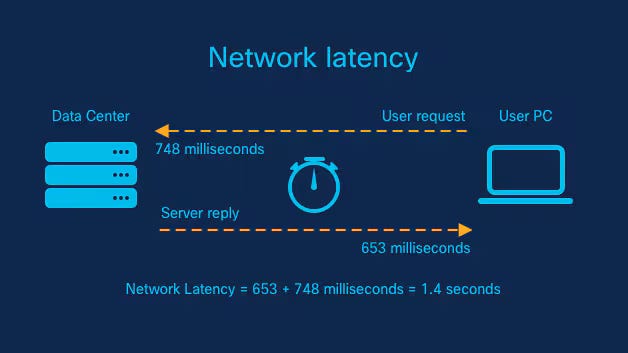
| Latency in Network Connection |
The Dynamic Host Configuration Protocol, commonly referred to as DHCP, is not without its fair share of drawbacks. While it offers the convenience and efficiency of automatic IP allocation, it also exposes networks to certain vulnerabilities.
It introduces potential security risks as unauthorized devices could potentially acquire an IP address from your DHCP server, thereby gaining access to your network. This means that any malicious user with basic understanding of how DHCP works can tap into your network which places a pressing need for additional security measures.
Another notable downside is the dependency on availability. In cases where the DHCP server faces downtime, new devices or those seeking IP lease renewal can’t access the network until service restoration, causing disruptive operation halts.
Then there’s the risk of IP address exhaustion. If too many devices request an IP address at once or if the lease time is too long, you may run out of addresses to assign. Similarly, excessive usage might hamper optimal performance leading to latency in network connections. Lease periods must be balanced to allow regular refreshing of IP addresses while preventing overloading the server with requests.
Lastly, management overhead cannot be overlooked. Keeping track of IP addresses assigned, reassignments, renewals and conflicts require significant administrative work if large numbers of devices dynamically join and leave the network. The manual intervention required primarily contradict one of the reasons for using DHCP; automation.
Though DHCP adds significant flexibility and control in managing networked devices, these drawbacks demand thoughtful consideration in specific use cases and scenarios. Therefore, whether DHCP is beneficial or detrimental depends largely on the nature of your network, the number of clients connecting and disconnecting frequently, and your ability to provide robust network security measures. Utilizing DHCP reservation1 can mitigate some of these issues by ensuring that specific devices receive the same IP address each time they request one.
Also consider lines of technical defense such as DHCP snooping2, which prevents unauthorized DHCP servers offering IP addresses, completing the network security circle in an environment where DHCP servers are used.
Remember, having a clear understanding of these limitations would better equip you to either troubleshoot existing problems or prevent potential issues in your network configuration. So, knowledge of such disadvantages can lead to a much stronger network design overall.
# Sample code snipet of a simple DHCP server configuration in Linux
# /etc/dhcp/dhcpd.conf
subnet 192.168.1.0 netmask 255.255.255.0 {
range 192.168.1.10 192.168.1.100;
option domain-name-servers ns1.example.org, ns2.example.org;
option domain-name "example.org";
option routers 192.168.1.1;
option broadcast-address 192.168.1.255;
default-lease-time 600;
max-lease-time 7200;
}
DHCP, or the Dynamic Host Configuration Protocol, is an essential part of any network. It simplifies the task of managing IP addresses by automatically assigning them to devices on a network. However, while DHCP brings many benefits to a network, it also has certain drawbacks which are worth noting.
First off, let’s delve into the increased administration overhead that DHCP may bring to network administrators. Although DHCP was designed with ease of management in mind, it might not always be the case. For instance, if you want a device to retain the same IP address each time it connects to the network, you have to set up a reservation in the DHCP server for that device’s MAC address. This kind of manual configuration can add administrative overhead, particularly on larger networks where hundreds or even thousands of reservations may be needed.
ip dhcp pool CLIENT host 192.0.2.1 255.255.255.0 client-identifier 01aa.bbcc.dd80.ba default-router 192.0.2.254 dns-server 192.0.2.2 lease 7
Moreover, the lack of static IP assignments could lead to potential vulnerabilities in the network security. Assigning static IP addresses allows for the use of Access Control Lists (ACLs) to manage network access at a granular level. With DHCP, this level of control is harder to achieve because the IP address of a device might change over time, making it difficult to keep track of which devices have access to specific areas of the network.
Another major drawback of DHCP can be seen in instances where the DHCP server goes down. Unless there are redundant servers in place, this could mean that new devices won’t be able to connect to the network and existing devices may lose connectivity once their lease expires, leading to network outage.
service dhcp ip dhcp excluded-address 192.168.1.1 192.168.1.10 ip dhcp pool mypool network 192.168.1.0 255.255.255.0 domain-name mydomain.com default-router 192.168.1.1 dns-server 192.168.1.2 lease infinite
Lastly, one subtle but potentially significant drawback of DHCP lies in its reliance on broadcasting. Particularly in wireless networks, too much broadcast traffic can degrade network performance. As DHCP relies heavily on broadcast messages to function (when a device first joins a network it broadcasts a request for an IP), in large networks the traffic created by these requests can become significant.
In general, understanding these pitfalls of DHCP can help in network planning. It necessitates features such as fault tolerance, secure DHCP implementation, as well as hybrid systems that mix dynamic and static IP addressing depending on the organizational requirements.
Here’s some source code to implement a simple DHCP Server using Python’s Scapy library:
from scapy.all import *
conf.checkIPaddr = False
fam,hw = get_if_raw_hwaddr(conf.iface)
dhcp_discover = Ether(dst="ff:ff:ff:ff:ff:ff")/\
IP(src="0.0.0.0",dst="255.255.255.255")/\
UDP(sport=68,dport=67)/\
BOOTP(chaddr=hw)/\
DHCP(options=[("message-type","discover"),"end"])
ans, unans = srp(dhcp_discover, multi=True)
for p in ans:
print p[1][Ether].src, p[1][IP].src
To learn more about DHCP and how it works, consider visiting online resources like Cloudflare’s Learning Center.The Dynamic Host Configuration Protocol (DHCP) has long been recognized as a solution to IP address management, providing significant benefits such as automated device configuration and straightforward network administration. But it’s important to acknowledge that alongside these advantages, DHCP carries with it several drawbacks and potential instability issues which can be problematic for the systems dependent upon it.
Network Security Risks
One of the most alarming shortcomings associated with DHCP is its insufficient security measures. By design, DHCP is an open protocol RFC 2131. This openness means that it is vulnerable to various types of network attacks, such as:
- DHCP Spoofing: In this scenario, an attacker sets up a rogue DHCP server on your network that responds to new node requests before your legitimate server.
- DHCP Starvation: Here, the attacker floods the DHCP server with requests until all available IP addresses are exhausted, preventing other devices from connecting.
Consider this snippet of Python code demonstrating a DHCP starvation attack using Scapy modules:
from scapy.all import *
def dhcp_starvation():
while True:
packet = Ether(src=RandMAC(),dst="ff:ff:ff:ff:ff:ff")/ \
IP(src="0.0.0.0", dst="255.255.255.255")/ \
UDP(sport=68,dport=67)/BOOTP(chaddr=RandString(12,'0123456789abcdef'))/ \
DHCP(options=[("message-type","request"),("server_id", "192.168.1.254"),("requested_addr", "0.0.0.0"),"end"])
sendp(packet)
dhcp_starvation()
This script fills in random source MAC addresses in Ethernet frames, generating numerous connection requests to exhaust the DHCP server’s pool of IP addresses.
Inaccurate Lease Times
Another noteworthy issue relates to DHCP lease times. If a server assigns too short a lease time, network traffic increases due to frequent renewal operations. Conversely, if leases are too long, then the efficiency of IP address usage is reduced – particularly concerning in networks with a lot of transient clients.
No Guarantee of IP Consistency
Also worth mentioning is the lack of existence of consistent IP assignments. There is no guarantee that a client will get the same IP address every time it connects. This dynamic nature can cause problems for services requiring a fixed IP like certain DNS configurations or server setups.
To illustrate, consider this table outlining hosts and their respective DHCP assigned IP addresses:
| Host | IP Address |
|---|---|
| A | 192.168.1.10 |
| B | 192.168.1.11 |
| C | 192.168.1.12 |
Should Host A disconnect from the network and subsequently reconnect, DHCP may reassign it a different IP address, say 192.168.1.13 – a shift that might not be compatible with some applications.
Overall Dependency
Lastly, there exists a broad issue of dependency on the stability of DHCP servers. If they happen to fail, new devices can’t join the network, and existing connections can struggle when it comes time to renew their leases. Not only does this limit network connectivity, but also points towards a single point of failure within the system.
As seen above, while DHCP provides significant aid to network management efforts, we cannot overlook these challenges. And as an evolving field, it’s crucial to continually assess new methods for mitigating these vulnerabilities, such as employing DHCP snooping or setting up failover DHCP servers – building more robust and secure network infrastructures altogether.Security risks associated with DHCP (Dynamic Host Configuration Protocol) usually arise from the protocol’s inherent trust of clients. This extends to a few key factors:
The Assignment of IP Addresses:
The most known functionality of DHCP is its ability to simplify network administration by automatically assigning IP addresses to devices on the network. However, this same facility has its drawbacks. Here are some related risks:
- DHCP Starvation attack: In this scenario, an attacker floods the DHCP server with DHCP requests and uses up all available IP addresses that the server can assign. Once exhausted, legitimate devices can no longer connect to the network.
- Rogue DHCP Server attack: Another drawback arises when an unauthorized DHCP server distributes invalid or duplicate IP settings. It can lead to unexpected behavior or even take down the entire network.
The Management of DNS Changes:
DHCP works hand-in-hand with DNS. When a device renews its DHCP lease, it might get a new IP address, and DHCP updates the DNS server accordingly. The following security risk relates to this function:
- DNS poisoning: Attackers deceive DHCP servers into the assignment of their intended DNS server (rogue DNS) to victims. This misdirection allows them to redirect users to fraudulent websites.
To circumvent these issues, certain measures could be taken such as implementing DHCP snooping or setting up DHCP security groups. Unfortunately, these solutions also come with drawbacks:
- Unintended blocking: Including additional security measures may inadvertently block legitimate devices if they fail to meet specified criteria.
- Additional setup and ongoing maintenance required: Deploying remedial actions requires upfront effort in configuration plus continuous monitoring which can tie up valuable IT resources.
Therefore, despite DHCP’s efficiencies, it has vulnerabilities that can make networks susceptible to malicious activities. Strategic planning must include potential threats associated with DHCP to prevent undesired outcomes.
Take a look at these examples:
Adding a DHCP Snooping binding table:
Switch(config)#ip dhcp snooping vlan 10 Switch(config)#ip dhcp snooping
Doing this configures the switch to consider DHCP messages coming from untrusted interfaces as invalid.
Establishing DHCP security group via Windows PowerShell:
New-DhcpServerv4Policy -Name "SecureGroup" -Condition OR -MacAddress EQ, "00-0C-29-12-34-56"
This code will only allow the device with the specified MAC address to obtain an IP address from the DHCP server.
For more information about DHCP-related vulnerabilities and countermeasures, you may refer to RFC 2131 or Microsoft’s official documentation for Windows PowerShell commands.
Remember, security is never a set-and-forget affair. Regularly patching, updating, and auditing configurations should part of routine operations. Always stay vigilant by staying informed about new vulnerabilities, exploits, and corresponding mitigation strategies.DHCP (Dynamic Host Configuration Protocol) is widely recognized for its ease of managing IP addresses. However, certain inherent limitations exist that frustrate scalability and can make DHCP slightly less suitable for expansion-bound organizations or large-scale projects.
Limited Scope:
The primary setback that hinders the full potential of DHCP occurs in virtue of its restricted scope capabilities, particularly when handling numerous subnets. Essentially, while DHCP operates incredibly well within a single subnet, diversions arise when you need it to extend beyond this boundary.
- In a majority of cases, you will want to assign different domain names, gateways, and lease times to clients connected on other networks. But with DHCP, this configuration comes more as an exception than a rule- creating plenty of extra work.
- Moreover, if your network needs grow beyond a single subnet but you do not intend to use a ‘Superscope’, you must manually configure each additional subnet. This could turn into a rather labor-intensive process requiring substantial technical proficiency.
Router(config)# ip dhcp exclude...
Router(dhcp-config)# default-router 192.168.1.1
Router(dhcp-config)# dns-server 8.8.8.8 8.8.4.4
Router(dhcp-config)# lease infinite
Scalability Issues:
The second drawback that significantly impairs DHCP’s efficacy is regarding its scalability.
- The biggest challenge arises when your subscriber base begins to multiply, primarily due to the insufficient number of IPv4 addresses. Given there are limited IPv4 addresses available, DHCP struggles to keep up with increasing demand because it can only allocate based upon what is available, which is rapidly diminishing.
- Furthermore, if your server infrastructure proliferates to the point where redundancy becomes necessary, this could pose an even more considerable quandary. While the DHCP protocol does provide failover support, it can be an immense undertaking to synchronize all changes between your servers.
Add-DhcpServerv4Failover -ComputerName "dhcpserver.corp.contoso.com" -Name "dhcpfailover" -PartnerServer
"dhcpserver2.corp.contoso.com" -ScopeId 10.0.0.0,
20.0.0.0 -LoadBalancePercent 50 -SharedSecret "P@ssw0rd" -AutoStateTransition $true
In summary, despite DHCP providing a high degree of automation for network configuration, one must caution against complacency. Be mindful of the likely hurdles as your company progresses such as DHCP’s limited flexibility when dealing with multiple subnets and its struggle to cope adequately under scalability circumstances.
For more information on DHCP and its known limitations, see “RFC 2131” titled ‘Dynamic Host Configuration Protocol’ that offers loads of useful insight.Unorchestrated network traffic is one of the key consequences of using Dynamic Host Configuration Protocol (DHCP). Imagine a symphony orchestra without a conductor to guide it or the correct sheet music for each instrument; it’s bound to sound dissonant and lose its coherence. The situation is much alike with unorganized network traffic, which results from the overuse or mismanagement of DHCP in network systems.
In essence, DHCP simplifies the task of assigning IP addresses to devices on a network by automatically distributing them from a central point. While this ease and automation can be hugely beneficial, they can also lead to a number of drawbacks:
1. Network Congestion:
One of the primary issues caused by DHCP usage is network congestion. As DHCP servers assign IP addresses dynamically, it becomes problematic if too many requests come at the same time. This could potentially cause server slowdowns or crashes, leading to network congestion and subsequent inefficiencies.
// DHCP request process // Step 1: DHCPDISCOVER - Client broadcasts to find DHCP servers // Step 2: DHCPOFFER - DHCP servers offer an IP address // Step 3: DHCPREQUEST - Client requests IP address // Step 4: DHCPACK - Server acknowledges and assigns IP address
2. Lack Of Accountability:
The automated distribution of IP addresses often leads to a lack of device accountability. It is difficult to track which device has been assigned which IP, and equally challenging to associate traffic to the exact device. In terms of security, it opens up opportunities for malicious actors to blend into the network nearly undetected, making DHCP networks highly susceptible to attacks and breaches.
3. Limited Customization:
While DHCP handles most typical network scenarios well, it may fall short when more intricate, customized network setups are required. Static IP allocations that need advanced configurations and settings are often not supported sufficiently through DHCP.
4. Dependency On DHCP Server:
Since every device initially communicates with a DHCP server to get an IP address, the entire networking environment becomes heavily dependent on it. Thus, any failure in the DHCP server could potentially bring the whole network to a standstill— a risk many organizations are unwilling to take.
5. Lease Renewal Issues:
When a DHCP server assigns an IP address to a device, it sets a ‘lease time’, after which the IP address must be renewed. However, if the device disconnects just before the lease expires and reconnects afterwards, it might obtain a different IP address, leading to inconsistent user experience.
In conclusion, while DHCP certainly offers convenience and simplicity in managing network IPs, the drawbacks underscore why careful planning and management are critical in using DHCP in network systems. To minimize these problems, a potential solution might involve using DHCP together with static IP assigning or considering alternative protocols like BOOTP (Bootstrap Protocol) or PPP (Point-to-Point Protocol).
Remember, orchestration is fundamental in maintaining harmony be it in an orchestra or a network system. Unorchestrated network traffic is not only a consequence but also a cautionary tale of improper DHCP usage.
When we’re discussing the pros and cons of Dynamic Host Configuration Protocol (DHCP), it’s essential to consider its dependence on servers for IP assignment. While this feature simplifies the IP address management process, it also presents several drawbacks that can impact network performance and administration:
Centralized failure point
Your network’s operability could be drastically affected if the DHCP server fails or encounters issues. Since a DHCP server dynamically distributes IP addresses, any malfunction in the server would halt new devices from joining the network.
class DHCP_Server {
public:
DHCP_Server() = default;
//...
private:
std::map> active_IP_addresses;
}
The example above shows a conceptual representation of how a DHCP Server might store assigned IP addresses. Any issue with “active_IP_addresses” map would stop the DHCP Server from correctly allocating IPs to clients.
Open to attacks
As the central component of the network, DHCP servers are likely targets for attackers. A common type of attack is the DHCP Starvation attack, where an attacker exhausts the IP address space available for legitimate hosts thereby causing denial of service.
Lack of static IP assignments
In some instances, such as setting up servers or other network equipment, IT professionals require static IP addresses. This fixed IP address approach goes against DHCP’s dynamic nature, forcing administrators to configure static assignments manually – another task that adds to their workload.
Inefficient use of IP address pool
Suppose there is a high turnover of devices connecting/disconnecting from the network, resulting in frequent DHCP requests. In that case, inefficient use of the IP address pool might occur — potentially leaving no available addresses when new devices attempt to connect. That happens because DHCP servers usually lease an IP address for a given period, and despite the client departing, the IP cannot be re-utilized until the lease expires.
Scalability challenges
Although DHCP servers are excellent at managing IP address assignments in smaller environments, they often pose scalability challenges when trying to accommodate larger, more complex networks.source. These challenges can lead to increased expenditure, both financially and time-wise, and compromise network efficiency.
Despite these potential pitfalls, network administrators often find the benefits of using DHCP -especially in automating the arduous task of manual IP assignments- outweigh the drawbacks. However, acknowledging these challenges is vital for planning, securing, and successfully maintaining any large-scale network environment.Communication failure due to an unavailable server response can lead to significant issues within a network system. This problem can arise from several sources, including problems with DHCP (Dynamic Host Configuration Protocol).
Let’s dive into the details about the scenario where communication fails because of an unavailable server response.
In an environment that uses DHCP, if there are too many requests coming in at once, the server could become overwhelmed and fail to respond in time. These requests could be for IP address allocations, renewals, or lease terminations.
In case of a single DHCP server setup, if the server goes down, all devices connected to it will lose their IP configurations. The downstream effect of this is communication failure across the entire network.
To illustrate this, let’s consider the following piece of code:
dhcprequest.on('close', function() {
throw new Error('DHCP server failed to respond');
});
When the server is unreachable, the code above throws an error “DHCP server failed to respond”.
In a busy network environment, congestion can affect the functionality of the DHCP server. If the network is clogged with traffic, there’s a chance that DHCP requests may not reach the server, leading to communication failure.
Consider the following DHCP related communication bottleneck:
if(network.congested) {
client.connection.terminate; //Terminates connection due to network congestion
}
In the above snippet, connections will get terminated when the network gets congested, implying communication failures.
A DHCP server with inadequate capacity may fail to serve DHCP requests efficiently. If the server storage is close to being full or if the processing capabilities of the server are low, communication failure might occur as the server becomes unavailable.
However, while addressing DHCP’s drawbacks could minimize the chances of unavailable server responses and communication failures, using strategic methods such as server clustering, load balancing, increasing server capacity, optimizing network infrastructure can offer more reliable solutions.
For a better understanding of DHCP drawbacks, you can refer to various resources available online, like IBM’s documentation on DHCP.
Remember, while the DHCP protocol provides convenient mechanisms for automatic configuration of IP addresses and other parameters, its limitations, when not properly addressed, can lead to serious communication failures. The key takeaway here is the importance of applying effective strategies to handle DHCP’s drawbacks in order to maintain seamless network communication.The Dynamic Host Configuration Protocol (DHCP) is an essential network service that automatically assigns IP addresses and other network configuration parameters to devices on a network. However, even with its considerable benefits, certain complexities arise during the lease renewal process of DHCP.
One of the complexities stems from the way DHCP leases work. When a client device links to a network, the DHCP server leases an IP address for a particular duration known as a lease period. This period could range anywhere between one day to forever. The problem arises when the device goes offline or leaves the network before the lease expiry. The DHCP server continues keeping the record and doesn’t release the IP address until the lease period ends which can lead to inefficient utilization of IP addresses.
Lease {
interface "eth0";
fixed-address 192.168.1.2;
option subnet-mask 255.255.255.0;
option routers 192.168.1.1;
renew 2 2000/1/12 00:00:01;
rebind 2 2000/1/12 00:00:01;
expire 2 2000/1/12 00:00:01;
}
A ‘DHCPREQUEST’ packet is sent halfway through the lease time to ask for an extension. But due to network congestion or lost packets, there is no absolute guarantee that the lease extension will reach the server in time. During peak network activity times, the request might fail, potentially booting devices off the network abruptly. If the DHCP server does not respond, the client must provide a new ‘DHCPDISCOVER’ packet, leading to increased network traffic.
Network security is another critical drawback on DHCP. Since the DHCP does not validate who requests the lease, malevolent clients posing as legitimate devices can acquire valid IP addresses. These rogue clients can exhaust the pool of available IP addresses, causing Denial of Service (DoS) attacks on new devices trying to join the network.
Finally, the DHCP’s centralized nature adds to its complexity. The DHCP server becoming unavailable would mean that no new connections could be made on the network. Although there are ways to mitigate this by using multiple DHCP servers, it increases the overhead and complexity as we then need mechanisms for these servers to sync up their leasing information.
In summary, while DHCP removes much of the manual work required for network management, mechanisms to handle lease renewal complexities, network security, and high availability need to be in place to mitigate potential issues.
For more about DHCP operation and drawbacks you might want to refer to “RFC 2131 – Dynamic Host Configuration Protocol“.It is essential to appreciate that, in a large network, overloading a single server can result in significant performance drawbacks. This is particularly the case with Dynamic Host Configuration Protocol (DHCP), a client/server protocol widely used on IP networks. DHCP automatically assigns an IP address and other related configuration settings to each device on the network, enabling them to connect to other IP networks. Though DHCP has numerous advantages, including automated network configuration, scalability, and lower IT overhead, it isn’t without its challenges. In this context we’ll dissect the drawback of DHCP’s potential to overload a single server.
One major issue due to overload on a single DHCP server stems from the fact that it might not be able to meet the high demand for IP addresses in a large network environment punctually. A single DHCP server is usually responsible for providing unique IP addresses to all connected devices. If one server receives too many assignment requests at once, it may struggle to process them efficiently, leading to slower response times and even missed IP lease renewals.
Consider the following code snippet that illustrates how the DHCP process works:
Obtain new IP address lease: Client — BOOTP/DHCP Request → Broadcast message DHCP Servers — BOOTP/DHCP Reply → Offer(s) IP Address Renew existing IP address lease: Client — BOOTP/DHCP Request → Unicast to leasing server DHCP Server — BOOTP/DHCP Reply → Extends lease
In a situation where multiple clients are making simultaneous requests, and there’s just one DHCP server, processing latency builds up leading to communications lags or complete drop-offs.
Another key issue emanating from DHCP server overload is redundancy or rather the lack thereof. When all requests are directed to a singular DHCP server – if it fails, the result is catastrophic for the network as no device will be able to obtain an IP address then. Subsequently, this translates to failure in connecting any new devices or reconnection of devices whose IP lease has expired nixing their access to the network.
A common practice to mitigate these issues is implementing DHCP failover. Essentially, it means setting up two DHCP servers with a shared pool of IP addresses. In an instance where one server goes down, the other springs into action ensuring unserved IP addresses don’t lead to connection lapses.
Consider a simple python based pseudocode for DHCP failover setup:
If primary_DHCP_Server fails: Activate secondary_DHCP_Server
Cloud-based DHCP services are another alternative where instead of handling DHCP in-house, it’s outsourced to a third party cloud provider cutting off internal server load.
The inherent challenge with a singular DHCP server portray the utmost importance of planning and strategizing to maintain smooth network operations and consistent device connectivity specifically for large networks with high device counts.
Ultimately, mastering an understanding of your DHCP configurations and consistently monitoring their performances does much to preempt substantial network failures due to DHCP server overloads. Keeping abreast with emerging trends in network protocols such as Software Defined Networking (SDN) could further allow you to alleviate these shortcomings through more efficient network management strategies.DHCP, also known as Dynamic Host Configuration Protocol, deploys IP settings to hosts on a network. It’s an extremely useful solution for managing and administering a substantial network infrastructure. Nonetheless, it has its pitfalls, one of them being Lag Time Problems arising from Lease Duration Management.
The Relationship Between Lease Duration and Lag Time
When a DHCP client connects to a network, it gets an IP address lease that is only transient. The time span for lease duration varies and can range from minutes to days, contingent on how the network administrator delineates it. When approaching the end of its lease duration, a DHCP client will attempt to renew its existing lease with the DHCP server.
Essentially, the unfortunate outcome may be a lag time problem, caused by the time consumed in this lease renewal process. Easing up on load times or reducing disruptions in network connectivity becomes challenging when any delay during lease renewal pops in.
Drawbacks Associated With Lease Duration Management in DHCP:
The following points sum-up some of the main drawbacks tied to lease duration with respect to DHCP:
- Excessive Network Traffic: Every time a lease renews, a series of interactions is set off between the DHCP server and client. This yields considerable network traffic, mainly if there are several DHCP clients on the network.
- Increased DHCP Server Load: Regular renewals put more strain on the server. In a large-scale environment, this means the server must process a pileup of requests, which may result in decreased performance or induce longer processing times.
- Potential Availability Problems: Any connectivity issue between the client and server during the lease renewal could lead to the client losing its IP address. This scenario would lead to losing network access until the issue resolves, meaning considerable downtime.
- Less Predictability for Network Management: Shorter lease durations make IP address allocation less predictable, making it laborious to plan and manage the network effectively.
- Client Disconnection Risks: If a device disconnects before its lease expires, the server will not liberate the IP address until the lease period consummates, which might elude IP addresses from other clients.
A recommended practice to circumvent these challenges significantly depends on the type of network you are managing. For smaller networks, elongating the lease duration can help minimize lease renewal rates and associated network traffic. Though so, bear in mind in large-scale environments – where IP addresses are more congested – shorter lease durations may be mandatory.
For example, you can adjust DHCP Leases durations in Ubuntu through:
# specify lease time in seconds default-lease-time 600; max-lease-time 7200;
Find the above-stated quote from NixCraft page about setting up a Linux/Unix DHCP Server.
Keep in mind that there’s no one-size-fits-all answer when it comes to adjusting DHCP lease durations. Striking a balance that minimizes network traffic while ensuring availability and optimal client performance usually requires some level of trial and error.
While DHCP (Dynamic Host Configuration Protocol) offers numerous benefits, including automated IP address management and efficient network administration, it’s essential to acknowledge that it is not without its drawbacks.
One significant drawback we observe with DHCP is the potential for IP address conflicts. When a DHCP server unintentionally assigns an already-in-use IP address to another device on the network, conflicts can arise, potentially causing connectivity issues.
// IP address conflict example dhcpcd[26745]: eth0: offered 192.168.1.100 from 192.168.1.1 dhcpcd[26745]: eth0: leased 192.168.1.100 for 86400 seconds dhcpcd[26745]: eth0: adding route to 192.168.1.0/24 dhcpcd[26745]: eth0: adding default route via 192.168.1.1 kernel: eth0: duplicate address detected!
Another disadvantage includes a reliance on the DHCP server itself. If the server goes down for any reason, new devices won’t be able to connect to the network until it’s back up and running, which might cause significant interruptions in productivity and workflow operation.
Moreover, on networks that require high security, DHCP may pose certain risks. As the server automatically assigns IP addresses, it becomes more challenging to track network activity linked to specific IP addresses.
Last but not least, a spontaneous change of a device’s IP address can also disrupt existing connections. For instance, an ongoing file download could be interrupted if the IP address gets changed midway.
For a better understanding of how DHCP operates, check out this link Disadvantages of DHCP – Comprehensive Study Guide.
In essence, while DHCP provides convenience and manages the network’s IP configuration with ease, these disadvantages should be considered when planning your network’s underlying structure and operations. Strategies for mitigating these drawbacks include having backup DHCP servers, consistent monitoring for IP conflicts, and additional security measures within the network infrastructure.