In the era of digital transformation, the backbone of every modern application, service, and remote workforce is the network. For decades, computer networking was a world of physical devices, manual configurations, and rigid architectures. Network engineers meticulously planned network addressing schemes using IPv4 and subnetting, configured routers and switches via command-line interfaces, and troubleshot issues by physically tracing network cables. While foundational concepts like the OSI Model, TCP/IP, and Ethernet remain critical, their implementation has undergone a seismic shift. Welcome to the world of Cloud Networking, where the network itself is software, defined by code, managed by APIs, and scaled on demand. This evolution is not just a technical upgrade; it’s a paradigm shift that enables unprecedented agility, automation, and even new business models, making it essential knowledge for any network engineer, DevOps professional, or system administration expert.
The Foundations of Modern Cloud Networking
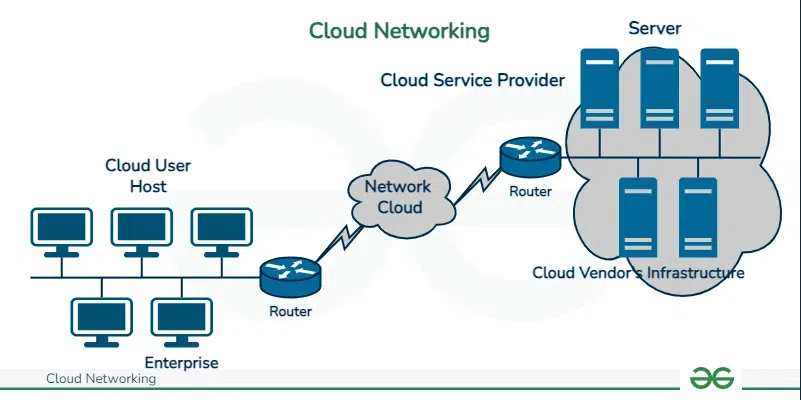
Cloud networking fundamentally abstracts the complex underlying physical hardware (routers, switches, network cables) and presents it as a virtualized, programmable resource. This is made possible by two core technologies: Network Virtualization and Software-Defined Networking (SDN). Instead of configuring individual network devices, we now define entire network topologies—from routing and switching logic to complex firewall rules—through software.
From Physical to Virtual: The Core Shift
The central component in most cloud environments is the Virtual Private Cloud (VPC) or Virtual Network (VNet). A VPC is a logically isolated section of a public cloud, giving you a private, secure space to launch resources. Within this VPC, you define your own network architecture:
- Subnetting: You carve your VPC’s IP address range (defined using CIDR notation) into smaller, manageable segments called subnets. This allows you to isolate resources, for example, placing public-facing web servers in a public subnet and secure databases in a private one.
- Routing: Route tables dictate how network traffic is directed. You can define rules that send traffic destined for the internet to an Internet Gateway, or traffic between subnets through the local network.
- Security: Network security is managed through virtual firewalls. Security Groups act as stateful firewalls at the instance level, while Network Access Control Lists (NACLs) provide a stateless firewall layer at the subnet level.
The beauty of this model is that all these components are software objects that can be created, modified, and destroyed programmatically via a REST API. This API-first approach is the cornerstone of network automation.
Practical Example: Creating a VPC with Python and Boto3
Let’s see how simple it is to create a foundational network component in AWS using Python’s Boto3 library. This script programmatically creates a VPC and a subnet within it, a task that would have once required manual hardware provisioning and configuration.
import boto3
import os
# Best practice: Use environment variables for credentials
# Ensure AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY are set
# Or use an IAM role if running on an EC2 instance
# Initialize the EC2 client
ec2_client = boto3.client('ec2', region_name='us-east-1')
def create_vpc_and_subnet():
"""
Creates a new VPC and a public subnet within it.
"""
try:
# 1. Create the VPC
vpc_response = ec2_client.create_vpc(
CidrBlock='10.0.0.0/16',
TagSpecifications=[
{
'ResourceType': 'vpc',
'Tags': [{'Key': 'Name', 'Value': 'automated-vpc'}]
}
]
)
vpc_id = vpc_response['Vpc']['VpcId']
print(f"Successfully created VPC with ID: {vpc_id}")
# Wait for the VPC to be available
waiter = ec2_client.get_waiter('vpc_available')
waiter.wait(VpcIds=[vpc_id])
print(f"VPC {vpc_id} is now available.")
# 2. Create a Subnet within the VPC
subnet_response = ec2_client.create_subnet(
VpcId=vpc_id,
CidrBlock='10.0.1.0/24',
AvailabilityZone='us-east-1a',
TagSpecifications=[
{
'ResourceType': 'subnet',
'Tags': [{'Key': 'Name', 'Value': 'automated-public-subnet'}]
}
]
)
subnet_id = subnet_response['Subnet']['SubnetId']
print(f"Successfully created Subnet with ID: {subnet_id}")
return vpc_id, subnet_id
except Exception as e:
print(f"An error occurred: {e}")
return None, None
if __name__ == "__main__":
create_vpc_and_subnet()Building Networks with Infrastructure as Code (IaC)

While scripting with libraries like Boto3 is powerful, the industry standard for defining and managing cloud infrastructure, including complex network designs, is Infrastructure as Code (IaC). Tools like Terraform, AWS CloudFormation, and Azure Resource Manager allow you to declare your desired network state in a configuration file. The IaC tool then intelligently interacts with the cloud provider’s API to make it happen.
The Declarative Advantage
IaC offers several key advantages over imperative scripting:
- Version Control: Your entire network architecture can be stored in Git, allowing you to track changes, collaborate with a team, and roll back to previous versions.
- Repeatability: You can deploy the exact same network configuration across different environments (dev, staging, prod) or regions with minimal effort, eliminating configuration drift.
- Visibility: The code serves as documentation, providing a clear, human-readable definition of your network design.
Practical Example: Defining a Network with Terraform
Here’s how you would define a more complete network in AWS using Terraform. This configuration creates a VPC, a public subnet for web servers, a private subnet for databases, an Internet Gateway to allow internet access, and a route table to direct traffic accordingly. This declarative approach is far more robust and maintainable for real-world network design.
# main.tf - Terraform configuration for a basic two-tier network
# Define the provider (AWS)
provider "aws" {
region = "us-west-2"
}
# 1. Create the main VPC
resource "aws_vpc" "main" {
cidr_block = "10.0.0.0/16"
enable_dns_support = true
enable_dns_hostnames = true
tags = {
Name = "production-vpc"
}
}
# 2. Create an Internet Gateway for public traffic
resource "aws_internet_gateway" "gw" {
vpc_id = aws_vpc.main.id
tags = {
Name = "production-igw"
}
}
# 3. Create a public subnet
resource "aws_subnet" "public_subnet" {
vpc_id = aws_vpc.main.id
cidr_block = "10.0.1.0/24"
availability_zone = "us-west-2a"
map_public_ip_on_launch = true # Instances get a public IP
tags = {
Name = "public-subnet-1"
}
}
# 4. Create a private subnet
resource "aws_subnet" "private_subnet" {
vpc_id = aws_vpc.main.id
cidr_block = "10.0.2.0/24"
availability_zone = "us-west-2b"
tags = {
Name = "private-subnet-1"
}
}
# 5. Create a route table for the public subnet
resource "aws_route_table" "public_rt" {
vpc_id = aws_vpc.main.id
route {
cidr_block = "0.0.0.0/0" # Route for all internet traffic
gateway_id = aws_internet_gateway.gw.id
}
tags = {
Name = "public-route-table"
}
}
# 6. Associate the route table with the public subnet
resource "aws_route_table_association" "a" {
subnet_id = aws_subnet.public_subnet.id
route_table_id = aws_route_table.public_rt.id
}Advanced Concepts: Automation, Security, and Performance
Once the foundational network is provisioned with IaC, the focus shifts to dynamic management, robust security, and performance optimization. This is where higher-level network automation and specialized services come into play, enabling everything from secure remote work for digital nomads to high-performance microservices.
Network Automation and Configuration Management
While Terraform is excellent for initial provisioning, tools like Ansible, Chef, or Puppet are often used for ongoing configuration management. For example, you could use an Ansible playbook to dynamically update firewall rules across a fleet of servers in response to a security threat, without ever manually logging into a console.
# ansible-playbook.yml - Example for updating a security group
- name: Update Web Server Security Group
hosts: localhost
connection: local
gather_facts: false
tasks:
- name: Allow SSH access from a specific IP
aws_ec2_security_group:
name: "web-server-sg"
description: "Security group for web servers"
vpc_id: "vpc-0123456789abcdef0"
region: "us-west-2"
rules:
- proto: tcp
from_port: 22
to_port: 22
cidr_ip: "203.0.113.5/32" # Your dynamic IP
- proto: tcp
from_port: 443
to_port: 443
cidr_ip: "0.0.0.0/0"
rules_egress:
- proto: all
cidr_ip: "0.0.0.0/0"Securing the Modern Network

Network security in the cloud is a multi-layered discipline. Beyond firewalls and VPNs, modern architectures for web services and microservices often employ a Service Mesh like Istio or Linkerd. A service mesh provides a dedicated infrastructure layer built right into an app. It controls how different parts of an app share data with one another, offering advanced features like mutual TLS encryption, fine-grained access controls, and detailed observability at the application layer (Layer 7 of the OSI model), which traditional network tools struggle with.
Network Monitoring and Troubleshooting
Troubleshooting in the cloud requires a different mindset. You can’t just plug in a laptop and run Wireshark to perform packet analysis on a virtual switch. Instead, cloud providers offer sophisticated network monitoring tools like AWS VPC Flow Logs, Azure Network Watcher, and Google Cloud Network Intelligence Center. These services provide detailed metadata about the IP traffic flowing through your network, allowing you to diagnose connectivity issues, detect anomalies, and audit network security rules. For deeper inspection, packet mirroring services can capture full packet data from specific instances for analysis with tools like Wireshark.
Best Practices, Optimization, and Future Trends
Building and managing a cloud network is an ongoing process of refinement and optimization. As applications scale and business needs evolve, the network must adapt. This is where advanced services and forward-looking strategies become critical.
Performance Optimization Strategies
To reduce latency and improve user experience, especially for a global audience, several technologies are key:
- Load Balancing: Distributes incoming traffic across multiple targets (e.g., virtual machines, containers) to ensure no single server becomes a bottleneck. Cloud load balancers are highly available and can scale automatically.
- Content Delivery Network (CDN): Caches content (images, videos, static files) in geographically distributed locations closer to users. This significantly reduces latency and offloads traffic from your origin servers.
- Edge Computing: Pushes compute and data storage closer to the sources of data. This is crucial for applications requiring real-time processing, such as IoT and connected vehicles, minimizing the round-trip time for data.
Monetizing the Network with APIs
One of the most exciting developments in cloud networking is the ability to monetize individual network features. By abstracting network functions into programmable services exposed via a REST API or GraphQL, providers can offer “network-as-a-service” products. For example, a telecommunications company could offer:
- On-demand, low-latency routing: A premium API call that guarantees a high-performance path for critical traffic.
- Dynamic DDoS mitigation: A service that customers can enable via an API call when they are under attack.
- Programmable VPNs: Allowing businesses to create and manage secure site-to-site connections entirely through an API.
This API-driven approach transforms the network from a cost center into a platform for innovation and revenue generation, a trend that is accelerating with the adoption of AI and machine learning for network management (AIOps).
Conclusion
Cloud networking represents a fundamental evolution in how we design, build, and manage the digital world’s infrastructure. The shift from physical hardware to virtualized, API-driven services has unlocked unparalleled levels of agility and automation. By embracing Infrastructure as Code with tools like Terraform, automating configuration with Ansible, and leveraging advanced cloud services for security and performance, we can build networks that are more resilient, scalable, and intelligent than ever before. For the modern network engineer or DevOps professional, mastering these concepts is no longer optional; it is the key to building the next generation of applications and services. The future of networking is not in a rack of blinking lights, but in a repository of well-written code.