The global internet relies on a complex, invisible handshake of agreements known as network standards. These protocols define how data moves from a sensor in a factory to a cloud server, or how a high-definition video stream reaches a mobile device with minimal latency. For any Network Engineer, DevOps Networking professional, or System Administration expert, understanding the evolution of these standards—from the foundational OSI Model to modern Edge Computing paradigms—is not just academic; it is essential for building scalable, secure systems.
As we transition into an era dominated by Cloud Networking and Microservices, the traditional boundaries of the Local Area Network (LAN) and Wide Area Network (WAN) are dissolving. Standards are shifting focus from hardware-centric routing to software-defined flexibility. This article provides a comprehensive technical deep dive into the protocols that power our world, exploring the intricacies of TCP/IP, the revolution of HTTP/3, and the implementation of Network Automation.
The Foundation: TCP/IP and the OSI Model
To master modern networking, one must first respect the legacy of the TCP/IP stack. While the OSI Model provides a theoretical 7-layer framework (Physical, Data Link, Network, Transport, Session, Presentation, Application), practical Network Architecture is built on the TCP/IP suite. The interaction between the Transport Layer (Layer 4) and the Network Layer (Layer 3) remains the most critical area for performance tuning.
Socket Programming and Protocol Implementation
At the core of Network Programming is the socket. Whether you are developing a VPN tunnel or a high-frequency trading bot, understanding how to manipulate sockets is vital. Socket Programming allows developers to interact directly with the NIC (Network Interface Card) and the operating system’s networking stack.
Below is a practical example of a multi-threaded TCP server in Python. This demonstrates how Network Standards dictate the handshake process (SYN, SYN-ACK, ACK) and data transmission. This is the bedrock of Application Layer protocols like HTTP and SMTP.
import socket
import threading
# Standard Loopback Interface address (localhost)
IP = '127.0.0.1'
# Port to listen on (non-privileged ports are > 1023)
PORT = 9999
def handle_client(client_socket):
"""
Handles the incoming client connection.
Implements a basic echo protocol standard.
"""
with client_socket:
request = client_socket.recv(1024)
print(f'[*] Received: {request.decode("utf-8")}')
# Simulate standard protocol response headers
response = "ACK: Message Received"
client_socket.send(response.encode("utf-8"))
def start_server():
"""
Initializes the TCP Server Socket.
Binds to IP/Port and listens for incoming connections.
"""
server = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
# SO_REUSEADDR allows the server to restart immediately after closure
# preventing the "Address already in use" error common in Network Troubleshooting
server.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)
server.bind((IP, PORT))
server.listen(5)
print(f'[*] Listening on {IP}:{PORT}')
while True:
client, address = server.accept()
print(f'[*] Accepted connection from {address[0]}:{address[1]}')
client_handler = threading.Thread(target=handle_client, args=(client,))
client_handler.start()
if __name__ == "__main__":
start_server()In this code, the `socket.AF_INET` specifies the IPv4 address family, and `socket.SOCK_STREAM` specifies the TCP protocol. Understanding these low-level primitives is crucial when performing Packet Analysis with tools like Wireshark or debugging Firewalls configurations.
Evolution of Web Standards: HTTP/2, HTTP/3, and QUIC
The HTTP Protocol has undergone massive shifts to accommodate the demand for lower Latency and higher Bandwidth efficiency. The move from HTTP/1.1 to HTTP/2 introduced multiplexing, header compression, and server push. However, HTTP/2 still relied on TCP, making it susceptible to Head-of-Line (HOL) blocking.
Enter HTTP/3 and QUIC. QUIC (Quick UDP Internet Connections) replaces TCP with UDP at the transport layer, handling reliability and congestion control in the user space rather than the kernel. This is a paradigm shift for Network Security and Load Balancing, as many legacy middleboxes (firewalls, NAT devices) are configured to drop or deprioritize UDP traffic.
Analyzing Network Addressing and Subnetting
Regardless of the transport protocol, efficient Network Addressing is non-negotiable. With the exhaustion of IPv4, the adoption of IPv6 is accelerating. However, dual-stack environments are common. A robust understanding of Subnetting and CIDR (Classless Inter-Domain Routing) is required for designing Virtual Private Clouds (VPC) and ensuring proper routing.
Here is a Python script utilizing the `ipaddress` library, a standard tool for Network Administration, to calculate usable hosts and subnets. This is frequently used in Network Automation scripts to provision cloud resources dynamically.
import ipaddress
def analyze_network(cidr_block):
"""
Analyzes a CIDR block to provide network details.
Essential for Network Design and Subnetting planning.
"""
try:
network = ipaddress.ip_network(cidr_block, strict=False)
print(f"--- Network Analysis for {cidr_block} ---")
print(f"Network Address: {network.network_address}")
print(f"Broadcast Address: {network.broadcast_address}")
print(f"Netmask: {network.netmask}")
print(f"Total IPs: {network.num_addresses}")
# Calculate usable hosts (Total - Network Address - Broadcast Address)
# Note: In AWS/Cloud, usually 5 IPs are reserved.
print(f"Usable Hosts (Standard): {network.num_addresses - 2}")
# Check if IPv4 or IPv6
if network.version == 6:
print("Protocol: IPv6")
else:
print("Protocol: IPv4")
# Example: Splitting the network into two smaller subnets
print("\n--- Subnetting Plan (Split into 2) ---")
subnets = list(network.subnets(prefixlen_diff=1))
for subnet in subnets:
print(f"Subnet: {subnet}")
except ValueError as e:
print(f"Error: Invalid Network Address - {e}")
if __name__ == "__main__":
# Example CIDR block often used in Docker or Cloud VPCs
analyze_network("192.168.10.0/24")
print("\n")
# Example IPv6 Block
analyze_network("2001:db8::/32")Cloud Networking, Edge Computing, and API Standards
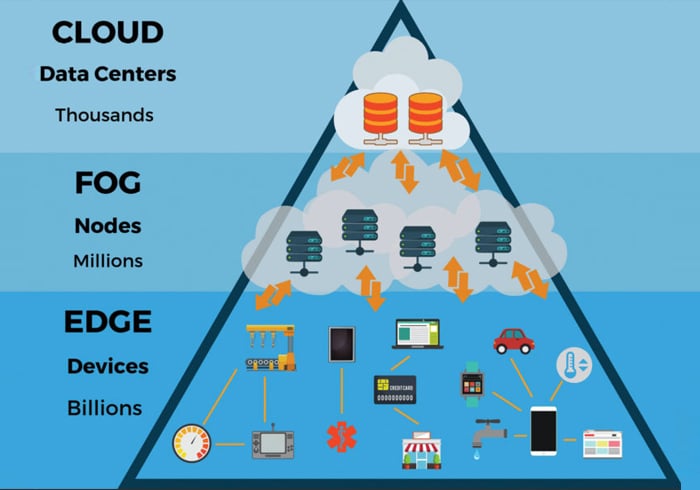
The centralization of the cloud is currently being complemented by the distribution of Edge Computing. In this architecture, computation moves closer to the data source (the “edge”), reducing latency for critical applications. This shift requires new Network Standards regarding Content Delivery Networks (CDN) and Service Mesh architectures.
API Design: REST vs. gRPC
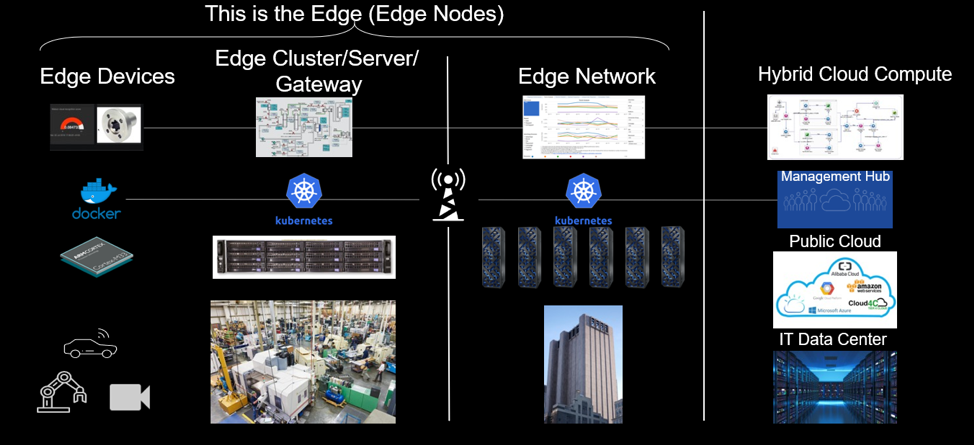
In a distributed edge environment, how services communicate is defined by API Design. While REST API (over JSON/HTTP) remains the standard for public-facing web services, internal Microservices often utilize gRPC (Google Remote Procedure Call). gRPC uses Protocol Buffers (Protobuf) for serialization, which is significantly lighter and faster than JSON, and runs over HTTP/2 by default.
This distinction is crucial for Network Performance. A Digital Nomad working with Travel Tech applications in remote areas with poor connectivity benefits immensely from the bandwidth efficiency of binary protocols like gRPC.
Below is an example of how a modern Network Engineer might structure a data schema using Protocol Buffers compared to a traditional JSON approach. This highlights the strict typing and efficiency standards of modern Network Development.
// --- 1. Traditional JSON Payload (REST API) ---
// Flexible, readable, but heavy on bandwidth due to repeated keys.
/*
{
"device_id": "router-edge-01",
"status": "active",
"metrics": {
"latency_ms": 12,
"packet_loss": 0.01
},
"tags": ["production", "us-east"]
}
*/
// --- 2. Protocol Buffers Definition (gRPC) ---
// Strictly typed, compiles to binary, extremely lightweight.
/*
syntax = "proto3";
package network_telemetry;
message DeviceStatus {
string device_id = 1;
enum State {
UNKNOWN = 0;
ACTIVE = 1;
INACTIVE = 2;
}
State status = 2;
message Metrics {
int32 latency_ms = 1;
float packet_loss = 2;
}
Metrics metrics = 3;
repeated string tags = 4;
}
*/
// --- Node.js Implementation Snippet for Edge Logic ---
const processTelemetry = (data) => {
// In an Edge Worker, we might validate standards compliance
if (data.latency_ms > 100) {
console.warn("SLA Violation: High Latency Detected");
// Trigger traffic rerouting logic here
}
return true;
};Network Automation and Software-Defined Networking (SDN)
Gone are the days of manually configuring Routers and Switches via CLI. Software-Defined Networking (SDN) and Network Virtualization have standardized the decoupling of the control plane from the data plane. Tools like Ansible, Terraform, and Python libraries (Netmiko, Napalm) allow for Infrastructure as Code.
Network Security is also automated. Standards like 802.1X for access control and IPSec for VPN tunnels are now deployed via policy scripts. For those in Tech Travel or remote work, Zero Trust network access (ZTNA) is replacing traditional VPNs, verifying identity at every request rather than just at the perimeter.
Automating Network Health Checks
To ensure compliance with Network Standards, engineers use automation to audit devices. The following Python script demonstrates a simple health check that could be part of a larger Network Monitoring pipeline. It simulates checking for open ports and service availability, a common task in Network Troubleshooting.

import socket
import time
def check_service_standard(target_ip, port, service_name):
"""
Verifies if a specific network service is reachable
and responding within acceptable latency standards.
"""
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.settimeout(2.0) # 2-second timeout standard
start_time = time.time()
result = sock.connect_ex((target_ip, port))
end_time = time.time()
latency = (end_time - start_time) * 1000 # Convert to ms
if result == 0:
status = "OPEN"
# Standard compliance check
quality = "Excellent" if latency < 50 else "Degraded"
else:
status = "CLOSED/FILTERED"
quality = "N/A"
sock.close()
return {
"service": service_name,
"ip": target_ip,
"port": port,
"status": status,
"latency_ms": round(latency, 2),
"quality": quality
}
if __name__ == "__main__":
# List of critical services to monitor
targets = [
("8.8.8.8", 53, "DNS (Google)"),
("1.1.1.1", 443, "HTTPS (Cloudflare)"),
]
print(f"{'SERVICE':<20} {'STATUS':<15} {'LATENCY':<10} {'QUALITY'}")
print("-" * 60)
for ip, port, name in targets:
data = check_service_standard(ip, port, name)
print(f"{data['service']:<20} {data['status']:<15} {data['latency_ms']:<10} {data['quality']}")Best Practices for Modern Network Design
Implementing these standards requires adherence to best practices to ensure robustness and security.
- Security First: Always implement HTTPS Protocol and TLS 1.3. Avoid deprecated versions like SSL or TLS 1.0/1.1. Use Firewalls (both network and web application firewalls) to filter traffic based on updated threat intelligence.
- Observability: Implement comprehensive Network Monitoring. Use standard protocols like SNMP or modern telemetry via gRPC to stream data to dashboards. You cannot optimize what you cannot measure.
- Redundancy and Failover: Design with failure in mind. Use Load Balancing standards to distribute traffic across multiple zones. For Wireless Networking and WiFi deployments, ensure channel overlap is minimized and roaming standards (802.11k/v/r) are enabled.
- Documentation: Maintain up-to-date network diagrams. Whether you are dealing with Ethernet cabling (Cat6/Cat6a) or virtual VPC peering, documentation is the first step in Network Troubleshooting.
Conclusion
The landscape of Network Standards is evolving rapidly. We are moving from static, hardware-defined architectures to dynamic, programmable, and distributed systems. The convergence of Cloud Networking, Edge Computing, and Security services is creating a new baseline for performance and scalability. For the modern Network Engineer or System Administration professional, the ability to write code (Python, Go, JavaScript) to interact with the network stack is no longer optional—it is mandatory.
By mastering the fundamentals of TCP/IP while embracing modern protocols like HTTP/3 and gRPC, and leveraging Network Automation, organizations can build infrastructure that is not only compliant with today's standards but ready for the innovations of tomorrow. Whether you are optimizing a global CDN or securing a remote connection for Travel Photography uploads, the standards discussed here form the digital nervous system of our connected world.